Control compliance and protection of your corporate data
Discover our out-of-the-box, automated approach to managing your data compliance and protection.
Personal data protection: together, anticipating the risk
Since 2018 and the implementation of the General Data Protection Regulation (GDPR) in Europe, personal data has value and therefore must be protected. It is now an unavoidable commercial and strategic issue for the companies that are responsible for it.
90% of consumers would not buy a product online or from an organization that does not demonstrate a commitment to protecting their data.
Of course, there are systems and technologies that natively guarantee this – secure databases, conditionally accessible software, etc. The challenge then also lies in the fact that the flow of data is changing. Data is no longer accessed only from a workstation protected by corporate security: it flows from telephones, personal computers and connected objects. This phenomenon of massification increases the risks of attacks or exfiltration. Companies must be able to control the circulation of data, determine who can access it, and how it is stored and protected.
To learn more, download the white paper in french Protection of personal data: together, anticipating the risk co-authored with Microsoft and DPO Consulting.
Download our white paper

Protection and governance of sensitive data, a major challenge for companies
The spread of teleworking, the multiplication of SaaS solutions to facilitate collaboration internally or with partners and customers, but also the multiplication of standards and regulations in terms of information protection, force organisations to deploy a range of strategies to improve their cybersecurity posture.
Through your Zero Trust approach, the protection and governance of your corporate data is an essential pillar.
The effectiveness of your security and compliance strategies brings together business, technical and legal stakeholders:
- DPO and Human Resources
- CIOs and CISOs
- Business managers
- Archivists and document managers
Your objective, with our support and expertise, is to be able to answer these four strategic questions:
- What are our sensitive and/or strategic data, and how can we track them at all times within our IS?
- In which use cases and with which individuals can these types of data be shared without the risk of breaching their confidentiality?
- When should we retain or delete data without the risk of losing the integrity of our business processes?
- How do we ensure compliance with our RGPD policy, ISO27001, or other local or international regulations?
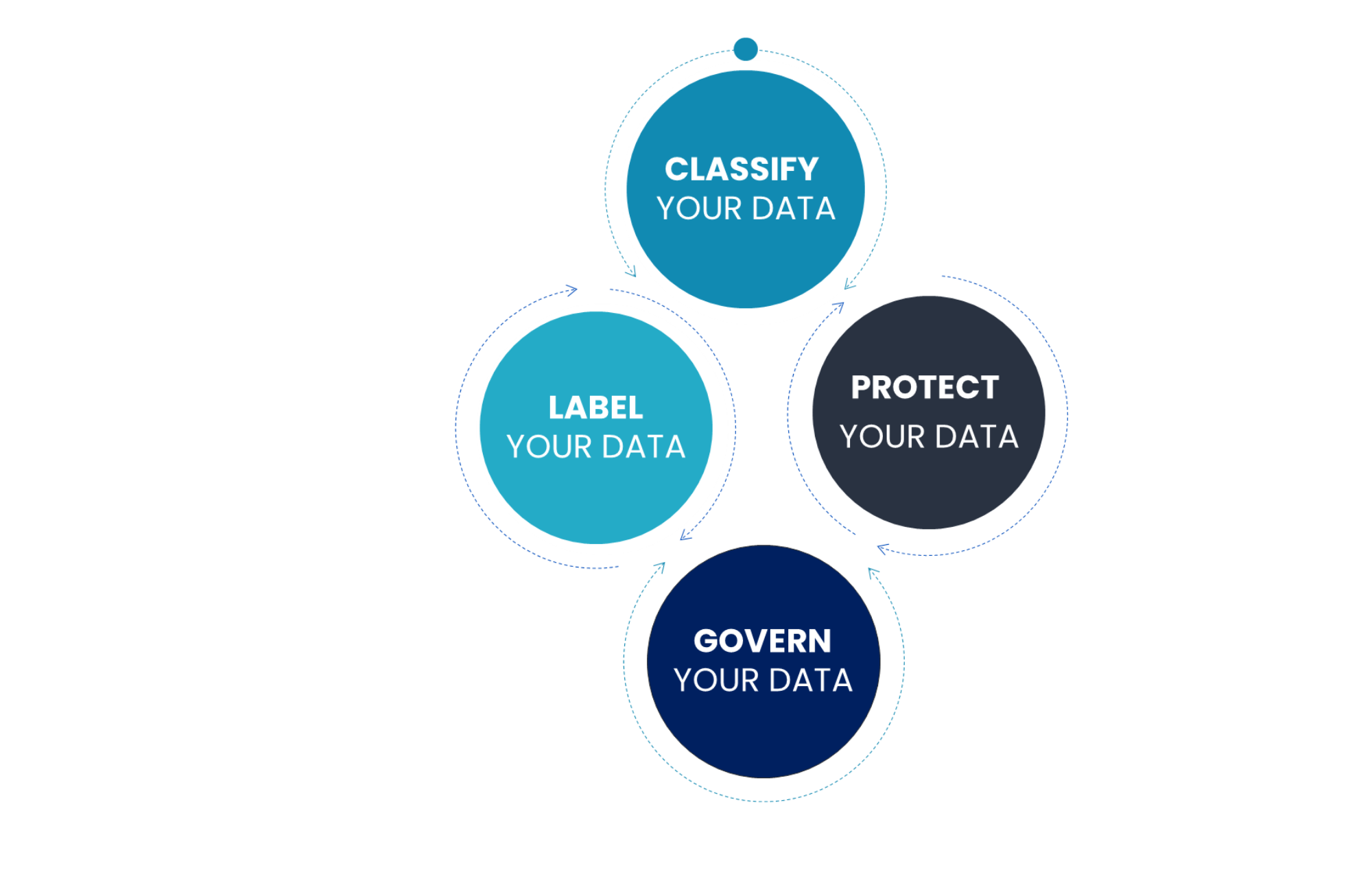
A ready-made approach to managing compliance and data protection
In order to answer these different questions in a controlled manner, Coexya applies an approach with you aimed at these 4 objectives :
1. Identify: Identify and classify your sensitive or significant data
2. Classify: Label the data according to its business nature and/or sensitivity
3. Protect: Control the exposure of data in a precise and automated manner
4. Govern: Store and delete data and records in a compliant and legal manner
Coexya supports you in an end-to-end approach to deploy and monitor your data protection and governance strategies
Our offer is adapted to your context to ensure a progressive, controlled and global deployment of your organisation. Our expertise combines consulting, integration and configuration, and support for change with your end users
- The audit phase allows us to map your data, on your Office 365 and/or On-Premise environments. A roadmap is defined together on the objectives to be reached and the associated priorities.
- Through use cases adapted to your context, we help you to experiment with different strategies and policies, whether they are protection or lifecycle governance oriented.
- We define and execute with you one or more pilot iterations to test the strategies previously considered, and identify improvements to be made before their deployment in production, for example: reduction of false positives and false negatives, measurement of the impact of the strategies on user adoption, processes and roles for monitoring incidents
- We support you in the progressive deployment and analysis of feedback from the field to optimise the quality of the strategies implemented
As ad-hoc support or through a managed services model, we help you monitor your data protection and compliance incidents and activities.
Our assets to support you in the governance of your data
You benefit from the business and technical expertise of Coexya’s teams throughout the process of your projects.
- Business approach: Mobilise and interview the strategic stakeholders of your project, according to the priorities you have defined : DPO, CISO, CIO, Archivists and document managers
- Functional approach: Present and explain the tree of possibilities in terms of solution configuration, in line with your current and future autonomy over these solutions
- Technical approach: Explain and advise on optimised deployment, taking into account any technical prerequisites and limitations
- User approach: Define a change management strategy that encourages end-users to adopt the protection and governance strategies that may impact their user experience.
- Management: with a commitment to results or technical assistance, we follow a rigorous project plan and manage the speed of your project, its risks and its budget with you.
- Expert and recognised integrator: our commitment to our publisher partners allows us to remain constantly up to date and to apply an approach that respects their deployment recommendations
Use Cases
For a client in the automotive industry
- Support, advice and testing of Microsoft Purview’s “Information Governance” capabilities
- Facilitation of “Discovery” sessions of Microsoft solutions to be considered
- Workshops to define a labelling strategy for retention purposes
- Construction, implementation and facilitation of a pilot project on document lifecycle governance through different use cases: manual/automated labelling, document deletion authorisation workflow, document archive management
For a banking solutions provider
- Progressive and continuous deployment of Microsoft Purview’s Information Protection & Governance capabilities: Classification, Protection Tagging, Retention Tagging, DLP
- Testing of Microsoft Purview Insider Risk Management capabilities: Information Barriers, Communication Compliance
- Definition, production and deployment of a change management strategy and plan to end users
- Application of the “Crwal, Walk, Run” approach to facilitate the empowerment of the project team and stakeholders within the IT and Security teams
For a leader in the food industry
- Audit of data at rest and in transit within the Office 365 tenant to measure the risk of non-compliance with the RGPD and other national regulations
- Setting up and activating probes with no impact on the end user
- Analysis and synthesis of results
- Presentation of short and medium term risks,
- Definition and estimation of a roadmap and Microsoft solutions to be implemented
For a leader in the pharmaceutical industry
- Carried out a pre-project pilot to measure the effectiveness of Microsoft’s solutions
- Automated identification of data associated with intellectual property: Keywords, RegEx, Document templates and machine learning
- Document tagging and user interaction: document enrichment through tagging, recommendation, automation
- Prevention of data leakage, internally or externally





